“Nine Emerging Minitrends to Watch” by Dr. John H. Vanston, MINITRENDS Author & Chairman, TFI
December 28, 2010
 Happy holidays to Minitrends blog readers! We appreciate your interest in our Minitrends posts and activities. As we start the new year, there will be many opportunities for those who are alert enough to recognize emerging trends, perceptive enough to realize their importance, and clever enough to take advantage of them. Here I suggest nine Minitrends—emerging trends that will become significantly important within 2-5 years, but are not yet generally recognized—that are well worth examining for possible action by those ambitious individuals who seek to start new ventures or keep existing businesses innovative and competitive.
Happy holidays to Minitrends blog readers! We appreciate your interest in our Minitrends posts and activities. As we start the new year, there will be many opportunities for those who are alert enough to recognize emerging trends, perceptive enough to realize their importance, and clever enough to take advantage of them. Here I suggest nine Minitrends—emerging trends that will become significantly important within 2-5 years, but are not yet generally recognized—that are well worth examining for possible action by those ambitious individuals who seek to start new ventures or keep existing businesses innovative and competitive.
Unlike megatrends, Minitrends are of a scope and importance to offer attractive opportunities to individual entrepreneurs, decision-makers in small and mid-size businesses, innovative thinkers in large companies, and adventuresome investors. In my new book, MINITRENDS: How Innovators & Entrepreneurs & Discover & Profit From Business & Technology Trends, I categorize the nine Minitrends below to those most applicable to different-sized groups. (In the book, I also discuss the background, current trends, and business opportunities of each of these Minitrends in more depth.) I do the same categorization below, but in reality, all provide opportunities to perceptive individuals in all-sized businesses.
Minitrends Particularly Applicable to Individuals or Small Groups of Individuals:
1. Expanding Involvement in Virtual Worlds (Free Virtual Worlds book excerpt available):
Virtual worlds are computer-based platforms that allow participants to engage in a wide range of real-world type activities, e.g., buying and building virtual world property, furnishing virtual world homes and offices, producing and selling virtual world goods, traveling, taking part in virtual world social activities such as parties and fundraisers, and communicating with other participants. Increasingly, virtual worlds are being used for educational purposes, product advertisements, new product modeling and testing, identification of new markets, and uncovering unexpected problems with new marketing programs.
2. Support for People Working at Home:
Although an increasing number of people are now conducting all or part of their work at home, these people often find they miss interacting with others and miss the convenience of facilities, equipment, and administrative support. A number of solutions are emerging to better meet the needs and desires of people working at home, including small offices or meeting rooms that can be rented by the day or the hour; chat rooms where people can meet informally to discuss ideas; semiformal groups that meet regularly to establish person-to-person interactions; and temporary support staffs organized to provide administrative assistance as needed.
3. Expanding Capabilities of Advanced Websites:
Although the World Wide Web had proven to be extremely popular, many believed a more interactive platform that took advantage of the Web’s power to communicate would be desirable (Web 2.0). Programmers are now expanding the capabilities of the Web to substitute computer activities for human activities, particularly activities that are repetitive, burdensome, and uninteresting (Web 3.0). Many believe Web 3.0 will eventually lead to effective artificial intelligence that can interact with humans in natural language.
Minitrends Particularly Applicable to Small and Medium-Size Companies:
4. Increasing Interest in Privacy:
Recent advances in technology, together with an increasing willingness of many to make personal information more easily available are threatening traditional concepts of privacy in terms of messaging, personal profiles, and identity. Techniques for countering these invasions of privacy, such as personal caution, technology aids, and group action are now being developed.
5. New Approaches to Giving and Receiving Advice:
Individuals and organizations commonly seek expert advice when making important decisions. In providing such advice, large consulting firms with large, multidisciplinary staffs, well-structured processes and procedures, huge computer capabilities, and long-standing reputations have traditionally had a major advantage. However, the ever-increasing power and ubiquity of information gathering, processing, and communicating technologies, small and medium-size consulting groups are often able to give more focused, timely, and user-friendly advice than the larger firms.
6. Evolution of Meaningful Maturity:
The twin trends of increasing life spans and decreasing retirement ages have caused a steady increase in retirement years. Because of social, personal interest, and/or financial reasons, many older individuals are either staying in their jobs longer or returning to the workforce. Their ability to utilize their experience, skills, and dedication effectively will depend on their current capabilities, their desires, and open opportunities to those willing to assist them.
Minitrends Particularly Applicable to Large Companies:
7. Advances in Digital Manufacturing:
Advanced digital manufacturing (ADM) processes build complex, custom-made parts by the addition of successive layers of material rather than traditional machining processes that cut, bend, and machine a part from stock material. The processes allow quicker production of prototypes and small production runs at a much lower cost. Recent ADM advances, including improved yield rates, reduced time-to-market, increasing variety of materials, and advances in 3D modeling software, have made ADM processes increasingly attractive to many manufacturers.
8. Increasing Electricity Use in Manufacturing:
The characteristics of electric power, such as high power density, no heat transfer medium requirements, controlled energy distribution, reduced material waste, and less environmental impacts, provide a number of benefits to manufacturing processes. Its use, however, has been limited by its relatively high cost. A number of factors, including advances in control technologies, changing customer needs, global competition, and increasing concern about the environment, are driving an increasing growth in the use of electricity in industrial processes.
9. New Applications of Nanotechnology:
When many substances are reduced to nano-size (100 nanometers or less) they often exhibit very different physical, electrical, chemical, and optical properties from the same substance at macro-size. These new properties often provide very unique and useful characteristics to nano-materials that can be used in a wide range of practical applications, such as cancer treatment, very high strength materials, special electronic systems, and water purification. Improved production techniques, decreased costs, and growing experience and understanding are increasing the practical applications of nanotechnologies
Minitrend involvement can give you a way to separate yourself from your colleagues and contemporaries. It provides a means for materially improving your business situation, your financial standing, and your personal satisfaction. I hope the Minitrends listed above will assist you or inspire you to launch your own exciting, profitable Minitrend Adventure that allows you to utilize your imagination, your logic, your innovative nature, and your basic good sense in the coming year.
Copyright 2011. Please feel free to reprint this article in whole or part with due credit to: “by Dr. John H. Vanston, MINITRENDS Author and Chairman, Technology Futures, Inc.” Thanks!
Denial of Service Attacks Spread in Web’s First InfoWar
December 9, 2010
 Nearly 20 years ago, when promoting a book called Secrets of a Super Hacker by an author named “The Knightmare,” I got a wake-up call about how vulnerable the Internet was. This week, many companies have learned how vulnerable they are after being shut down by hackers related to the WikiLeaks drama.
Nearly 20 years ago, when promoting a book called Secrets of a Super Hacker by an author named “The Knightmare,” I got a wake-up call about how vulnerable the Internet was. This week, many companies have learned how vulnerable they are after being shut down by hackers related to the WikiLeaks drama.
Yesterday, MasterCard’s website was shut down for hours by a group of hackers angry that the credit card company had ceased processing payments to WikiLeaks. Andy Greenberg has been following this story minute-by-minute on The Firewall, his computer security column for Forbes:
MasterCard, which cut off services to WikiLeaks Tuesday, became the latest victim of a loose group of hackers known as Operation: Payback Wednesday morning, when its website went down under a flood of junk traffic sent by the group’s volunteer army… PayPal has already come under two cyberattacks after its decision to cut off its services to WikiLeaks last Friday night… And now PayPal may be back on its target list, followed by Twitter.
The technique being used in these attacks is a “Distributed Denial of Service” attack, or DDoS. The idea is to temporarily take control of thousands of computers on the Internet and direct them to a single Web address, causing the site to falter and eventually shut down. This technique was used by a hacker named “Jester” to shut down WikiLeaks in November. It’s the same technique being used by “Operation: Payback” and a group of hackers named “Anonymous” (a.k.a. “4Chan”) to retaliate against companies such as Amazon, PayPal, Visa, and others who have severed support services to WikiLeaks.
If you’re wondering what it’s like enduring a DDoS attack, Bill Brenner, the information security expert for CSO Magazine, provides a minute-by-minute account of the July 4, 2009, cyberattack that took out the Federal Trade Commission’s website, along with the Department of Transportation, and many private companies:
In that onslaught, a botnet of some 180,000 hijacked computers hammered U.S. government websites and caused headaches for businesses here and in South Korea.
This is the infamous attack that caused Google to publicly blame Chinese hackers, leading Google to eventually move its servers out of mainland China. By way of comparison, the attack on WikiLeaks last week was estimated at nine times larger than the infamous Fourth of July attack. Ironically, one of the 250,000 diplomatic cables recently released by WikiLeaks implicates the Chinese government in the Fourth of July attacks.
In a tweet on December 3 related to the WikiLeaks hackathon, Electronic Frontier Foundation co-founder John Perry Barlow uttered the syllables many a CIO has feared: “The first serious infowar is now engaged.” Barlow was one of the experts I approached in 1993 to review the book, Secrets of a Super Hacker.
The promotion for that book included a contest offering a prize to the first person who could hack my email account and send an email from my own account claiming the prize. When I first proposed the contest, the publisher’s Internet Service Provider (ISP) immediately notified all their subscribers, resulting in such an outcry that we decided to move the contest. Next, I approached The WELL, the cybercommunity in San Francisco where Barlow and many now famous members of the digerati hung out.
The WELL wanted no part of our contest, either, and threatened to suspend our account if we tried to run it there. I thought they would be pleased to have this benign test of their security systems. Instead, The WELL and several other ISPs I approached wanted no part of our hacking contest. Why?
After discussing the situation with several ISP administrators, I realized that security was not a priority for many of them. Most of them were using whatever weak protection came standard with the software they bought. They did not want their systems tested. If they had any extra money, they spent it on marketing: sprucing up the front door, not patching up the back door.
Our little contest served as a wake-up call for several service providers at the dawn of the Internet era. The infowar between WikiLeaks’ opponents and defenders should act as a loud wake-up call to online organizations everywhere to check their defenses. Cyber warfare has come of age, and the stakes now are higher than anyone imagined.
STEVE O’KEEFE
News Editor, Minitrends Blog
Source: “MasterCard Taken Down By WikiLeaks Supporters, Twitter Next?,” Forbes, 12/08/10
Source: “What it’s like to get hit with a DDoS attack,” CSO Magazine, 12/08/10
Source: JPBarlow on Twitter
Image: Book cover of Secrets of a Super Hacker is used under Fair Use: Reporting.
FTC Advocates Do-Not-Track; Advertisers Upset
December 3, 2010
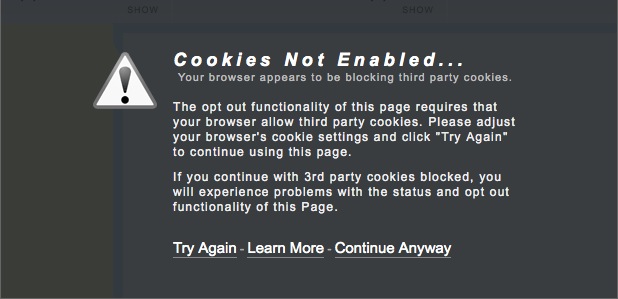
Screen capture from the Interactive Advertising Bureau's "AboutAds.info" opt-out page. To install the IAB's opt-out software, users must expose their browser to significant privacy risks by enabling cookies.
On December 1, the U.S. Federal Trade Commission presented a preliminary report (PDF) outlining a “framework for privacy” that endorses a “Do-Not-Track” option for Web browsers similar to the agency’s popular “Do-Not-Call” service for telephones.
Unlike the Do-Not-Call program, which creates one central place where individuals can easily add their phone numbers to the list, with reprisals for companies that violate their preferences, the Do-Not-Track mechanism (“DNT”) will be built into the Web-browsing software and other applications used to access the Internet from computers, tablets, and smartphones. Each piece of software or app would have to include a DNT feature. Currently, there are no proposed guidelines for consistently implementing that feature, nor any real authority to enforce it.
Forbes‘ new privacy blogger, Kashmir Hill, says, “At the end of the day, this report isn’t going to change anything.” Kevin Fogarty, the highly opinionated blogger for ITworld‘s “CoreIT” blog, is blunt in his assessment, calling the FTC report:
[…] a set of recommendations with roughly the same clarity, credibility and impact of a strongly worded letter from the U.N. to this year’s evil dictator asking him to please not kill and eat so many villagers.
At The Huffington Post, consumer rights activist Jamie Court threatens a privacy initiative in California: “If Congress doesn’t act, we will go to the ballot.”
While Internet giants, including Google and Microsoft, have learned to tame their public pronouncements and pay lip service to the FTC’s recommendations, they let the trade groups they fund do the barking for them. Mike Zaneis, senior vice president and general counsel of the Interactive Advertising Bureau (IAB), is quoted by The New York Times media reporters Edward Wyatt and Tanzina Vega as saying that the DNT mechanism will cause “significant economic harm” if it has “a high participation rate similar to that of do not call.”
The IAB is recommending voluntary measures where sites place prominent “opt-out” buttons that disable tracking, rather than a central registry or browser build-ins. The organization touts its AboutAds.info site, where you can opt out of being tracked by a very small group of sites that participate.
John and Carrie Vanston devote a major section of their new book, MINITRENDS, to business opportunities arising from increasing interest in privacy. They predict that the U.S. will strengthen its privacy laws, opening up profitable new business lines for entrepreneurs:
The federal government of the United States has adopted only limited formal legislation to protect privacy compared to Canada and most European countries.
Among the businesses that will profit from strengthening privacy laws are software developers, training firms, and the new field of online reputation management companies.
Certainly, someone needs to come up with a solution better than the IAB’s “opt-out” site. When this reporter visited the site to test the opt-out features, I was advised I would have to enable cookies in order to install the software (see screen capture, above). While enabling cookies would protect me from being tracked by few dozen sites participating in the IAB’s program, it would open me to tracking by the millions of sites that not only don’t participate, but sometimes use methods that are much more intrusive than those of IAB’s supporters — methods which remain, unfortunately, virtually unregulated.
STEVE O’KEEFE
News Editor, Minitrends Blog
Source: “Protecting Consumer Privacy in an Era of Rapid Change” (PDF), Federal Trade Commission, 12/10
Source: “Brief Takeaways — and a Pretty Diagram — from the FTC’s Online Privacy Recommendations,” Forbes, 12/01/10
Source: “FTC becomes aware there is an Internet,” ITworld CoreIT Blog, 11/17/10
Source: “Will We Get a ‘Do Not Track Me’ List for Our Personal Information Online?” The Huffington Post, 12/01/10
Source: “F.T.C. Backs Plan to Honor Privacy of Online Users,” The New York Times, 12/01/10
Source: MINITRENDS How Innovators & Entrepreneurs Discover & Profit From Business & Technology Trends, p. 97.
Image from AboutAds.info, the Interactive Advertising Bureau’s “opt-out” site, screen capture recorded 12/02/10. Used under Fair Use: Commentary.
Is Microsoft’s Kinect the New Trend in Advertiser Black Ops?
November 16, 2010
 The chief operating officer for Microsoft’s Xbox division ignited a firestorm of controversy last week when he told a room full of digital entertainment investors about the capabilities of the Xbox’s revolutionary new motion controller, Kinect, to target advertising based on what built-in cameras see.
The chief operating officer for Microsoft’s Xbox division ignited a firestorm of controversy last week when he told a room full of digital entertainment investors about the capabilities of the Xbox’s revolutionary new motion controller, Kinect, to target advertising based on what built-in cameras see.
Kinect launched November 4 as a hands-free device for playing video games. Unlike other video game consoles, such as Wii and PlayStation, Kinect allows users to play Xbox games without having to hold a motion-detecting controller. Kinect senses your motions using multiple cameras and infrared detectors.
Dan Gallagher, technology editor for The Wall Street Journal‘s MarketWatch subsidiary, reported on Dennis Durkin’s remarks on the Journal‘s Digits blog last Thursday. Gallagher quotes Durkin as saying that Microsoft “can cater which content we present to you based on who you are.” The Journal, part of Rupert Murdoch’s News Corp, which owns Fox News among many other media assets, has become an unlikely privacy champion after the newspaper’s “What They Know” series last July blew the lid off privacy invasions by the Internet’s top websites.
Immediately after the unfavorable coverage in The Wall Street Journal, Microsoft issued a statement contradicting Durkin’s remarks. The statement, which strangely does not appear on Microsoft’s Xbox Press page, reads in part:
Xbox 360 and Xbox LIVE do not use any information captured by Kinect for advertising targeting purposes.
However, other websites have published more of Dennis Durkin’s remarks, and it appears unlikely that his remarks at the BMO Capital Markets Digital Entertainment Conference were a simple slip of the tongue.
Bill Levine at TopTechNews quotes the Xbox CEO as stating the controller can tell “how many people are in a room when an advertisement is shown,” and that it can use “face recognition and voice recognition” to determine such things as the gender of players, whether or not they are standing, and how excited they are.
Molly McHugh at the Digital Trends blog quotes Durkin as stating flatly that data gathered by the Xbox’s cameras can be used to customize ads. Microsoft can “be more targeted about what content choices we present; what advertising we present….”
The capabilities of the Xbox Kinect to spy on users and then use that information to customize ads is part of a growing technology trend. The screens we watch at home and at work are now watching us — and using that information to customize the content and the ads we see.
In September, two of The Wall Street Journal‘s correspondents in Japan, Daisuke Wakabayashi and Juro Osawa, reported on a futuristic vending machine in a train station there that uses cameras to determine the gender and age of people using the vending machine. The machine then recommends selections based on that information.
The vending machine, manufactured by NEC, records such things as which people looked at which items, who bought what, and how “engaged” they were with the display. According to the Journal‘s reporters:
The company said its system can identify people’s gender correctly about 90% of the time and guess a person’s age within a 10-year range about 70% of the time.
The Journal notes that there are few, if any, laws governing the collection, storage, and use of images and information gathered by such devices. The technology is expected to show up in retailers’ window displays soon. Those displays will change the merchandise being shown depending on who is looking at them.
These kinds of invasions of privacy were anticipated in the new book, MINITRENDS, by John & Carrie Vanston. The authors suggest that privacy protection will be one of the booming technology trends in the coming two-to-five years, and devote a significant portion of the book to describing opportunities for entrepreneurs in this rapidly evolving segment of the economy.
What do you think about store displays that watch you and record your image and actions as you shop? Do you think they should be allowed? Do you think they can be stopped? Do you see any technologies coming in the next two to five years that could protect people from these devices? We’re anxious to hear your comments on these matters.
STEVE O’KEEFE
News Editor, Minitrends Blog
Source: “Is Your Xbox Console Watching You?” The Wall Street Journal, 11/12/10
Source: “Big Brother Kinect Could Be Watching You at Home,” TopTechNews, 11/12/10
Source: “Kinect’s camera could record data for advertisers,” Digital Trends, 11/12/10
Source: “Billboards That Can See You,” The Wall Street Journal, 09/03/10
Image courtesy of quatro.sinko, used under its Creative Commons license.
Information Security Victim to IT Trends
November 9, 2010

Lured by the prospect of reduced costs, more companies are putting their information assets at risk by embracing technology trends such as cloud computing. A new survey finds that companies are failing to assess these risks and take defensive measures.
Consulting giant Ernst & Young released its 13th annual Global Information Security Survey last week, and the privacy picture that emerges is not good. The Vancouver Sun summarizes the findings this way:
Less than a third of global businesses have an IT risk management program capable of addressing the risks related to the use of new technologies… In spite of the rapid emergence of new technology, just one in ten companies consider examining new and emerging IT trends a very important activity for the information security function to perform.
What are the IT trends eroding information security at major corporations?
Mobile Computing, including smartphones, tablets, and laptop computers: “Devices that can contain information are increasingly prevalent; they are used for both work and home purposes, blurring the lines between the two, and results in ceding of control over the devices and the information to employees, service providers and others.”
Cloud Computing, including Software-as-a-Service (SaaS): “While organizations may have chosen in the past to avoid cloud technologies and the possible privacy and security challenges they bring about, in this economic climate, the cost reduction benefits that such solutions offer have brought many organizations to reassess whether these transformational technologies are right for them.”
Social Networking and other “Web 2.0” technologies: “60% perceive increased risk from the use of social networking.”
In their new book, MINITRENDS, John and Carrie Vanston cite increased interest in privacy as one of the most promising areas for entrepreneurial activity in the coming two-to-five years:
In general, communications and computer technologies designed to gather personal information have progressed more rapidly and dramatically than those designed to protect this information. Serious efforts are being expended, however, to develop protection technologies.
The authors suggest some of the avenues for Minitrend development, including making it easier for employees to use privacy-protection software and teaching employees how to protect sensitive information. This insight is bolstered by the Ernst & Young report, in which a whopping 92% of respondents indicate that employee awareness of security issues is a problem.
Information security was a lot easier when it was a matter of protecting the perimeter around a company’s information assets. But in today’s economy, those information assets are widely distributed and stored in the hands of employees and outside vendors, making it much more difficult for organizations to protect them. Clearly, Ernst & Young’s shocking report shows tremendous opportunity for innovators and entrepreneurs who can develop technological solutions to modern privacy problems.
STEVE O’KEEFE
News Editor, Minitrends Blog
Source: “Ernst & Young Report Reveals Companies Unprepared to Address Risks Created by New Technology,” The Vancouver Sun, 11/04/10
Source: “Top privacy issues for 2010,” Ernst & Young, 02/10
Source: “Emerging Technology Trends Increase Risks of Protecting Corporate Information,” PR Newswire, 11/04/10
Source: MINITRENDS: How Innovators & Entrepreneurs Discover & Profit From Business & Technology Trends, Technology Futures, Inc., p. 95.
Photo by D. Sharon Pruitt (Pink Sherbet Photography), used under its Creative Commons license.


